Network monitoring is essential for IT management, ensuring efficiency, security, and stability by tracking network activity in real time. It helps detect issues, prevent downtime, and maintain performance by providing visibility into traffic, security threats, and system health. As IT infrastructures grow more complex, effective monitoring optimizes resources, enhances security, and supports compliance across on-premises, cloud, and hybrid networks.
What is Network Monitoring?
Network monitoring involves tracking and analyzing the activity within a computer network to ensure optimal performance, security, and availability. Various network monitoring tools help assess traffic patterns, service availability, and performance metrics. This process is essential for detecting intrusions, identifying anomalies, and ensuring smooth network operations.
Network administrators rely on network monitoring software for several critical tasks, including:
- Identifying network issues;
- Detecting security threats;
- Monitoring ongoing cyber-attacks;
- Evaluate the effect of security incidents;
- Tracking network modifications;
- Analyzing usage patterns;
- Maintaining log records;
- Receiving alerts on unusual activities.
How Network Monitoring Works
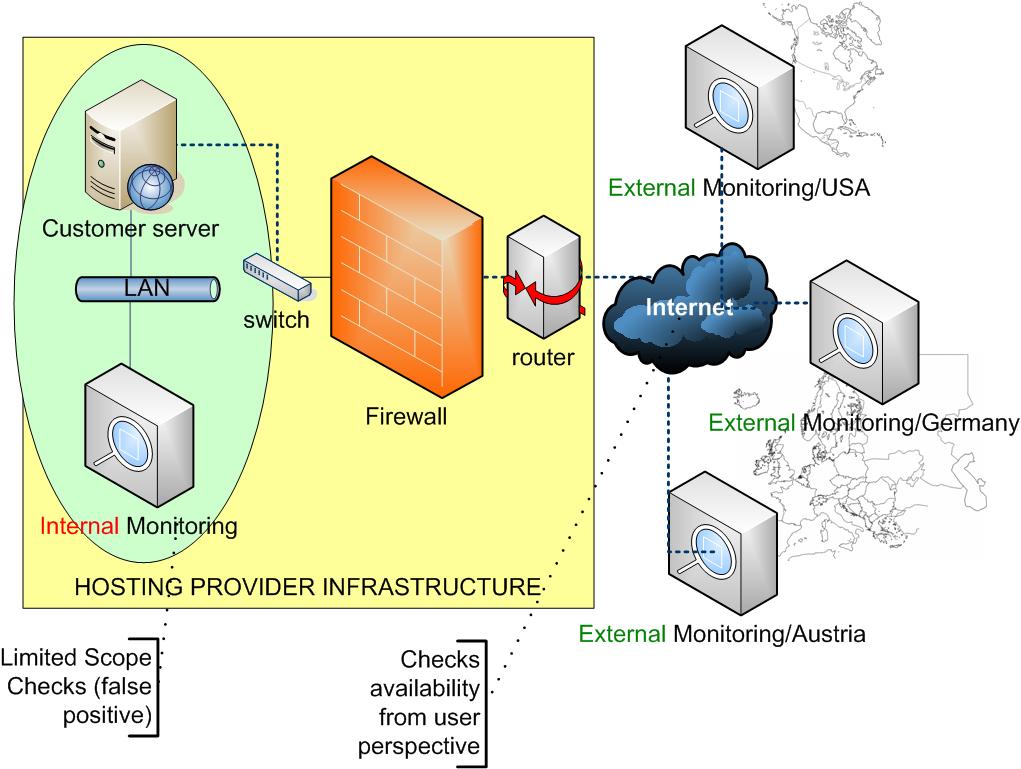
Network monitoring tools analyze data from connected devices, recording communication details, traffic flow, and system activities. Administrators then review this data to identify potential issues or security risks.
Network monitoring solutions are often divided as two types:
- Passive monitoring: Involves collecting data without actively engaging with equipment. While less expensive, it may not identify security problems as well;
- Active Monitoring: Probes are used to assess network performance and security by producing traffic and evaluating the answers. This approach delivers more detailed information, but it may need more hardware.
Effective network monitoring supports network health, finds vulnerabilities, and eliminates service disruptions, resulting in a secure and efficient IT infrastructure.
Advantages of Network Monitoring
Avoid Downtime with Proactive Monitoring
IT outages can result from human error, misconfiguration, or external factors. Network monitoring helps to reduce these risks by giving real-time visibility into network performance. Potential bottlenecks and service disruptions may be discovered and corrected before they become more severe using an easy dashboard that displays real data.
Resolve Issues Quickly
When there is network disruption, every second matters. Network monitoring makes troubleshooting easier by determining the core cause of problems, whether it’s a configuration error or an odd surge in traffic. Live network maps and performance measurements offer rapid insights, minimizing reaction time. Furthermore, automation technology may detect and resolve errors without the need for user engagement.
Improve Efficiency and Cost Savings
IT teams frequently encounter increasing workloads despite limited resources. A network monitoring system provides immediate benefits by reducing the need for time-consuming manual troubleshooting. Staff may focus on more strategic objectives by swiftly detecting performance concerns, increasing productivity, and lowering operating expenses.
Adapt to Expanding and Evolving Networks
With the fast proliferation of linked devices and developing IT infrastructures, networks are becoming increasingly complicated. By 2027, the total number of IoT-connected devices is estimated to exceed 29 billion. Network monitoring guarantees that wireless devices, cloud-based systems, and remote work setups run consistently and securely. It gives the necessary flexibility to manage cloud migrations, IPv6 transitions, and remote access management, ensuring that operations run smoothly even in the face of rapid change.
Detect Security Threats
For organizations that cannot afford specialist intrusion detection software, network monitoring is a vital first line of defense. Monitoring tools help spot abnormalities such as odd traffic spikes or illegal devices attempting to connect by providing a baseline for regular network behavior. Early identification helps to reduce possible security vulnerabilities before they worsen.
Support Data-Driven Upgrade Decisions
IT budgets frequently demand justification for hardware changes. Network monitoring technologies give historical performance data, allowing IT professionals to deliver objective findings rather than depending on intuition. Organizations can decide if their present infrastructure can accommodate future needs or if they need to invest in new technology by reviewing historical trends.
Ensure SLA Compliance
IT consultants and managed service providers must adhere to service-level agreements (SLAs). Network monitoring allows for real-time observation of network performance, making it simpler to show uptime, availability, and dependability to clients. Businesses may preserve confidence and meet contractual obligations by dealing with difficulties proactively.
Maintain Regulatory Compliance
Regulations such as FISMA, SOX, and PCI-DSS require firms to monitor network activities in order to secure sensitive data. Network monitoring tools assist in tracking security measures, logging network activities, and ensuring compliance with industry standards. Keeping accurate logs of network activities not only protects firms from fines, but also improves overall cybersecurity.
Key Stages of Network Monitoring
The network monitoring process follows a structured five-stage framework to ensure optimal performance, security, and functionality. These stages include auto-discovery, performance management, alarm and event management, configuration management, and network traffic analysis. Each stage plays a vital role in maintaining a reliable and efficient network.
Auto-Discovery
Auto-discovery automates the identification and mapping of all connected devices, helping IT teams define the monitoring scope and ensure efficient oversight.
Performance Management
Performance management tracks network stability using real-time insights and historical data, allowing IT teams to detect issues early and anticipate future capacity needs.
Alarm and Event Management
Alarm and event management captures and processes network incidents, ensuring anomalies are logged and addressed promptly. Alerts are sent via email, SMS, or ticketing systems, allowing quick corrective action.
Configuration Management
Configuration management prevents misconfigurations and minimizes downtime by automating backup and restoration of device settings. This ensures stable configurations are available when needed, reducing manual work.
Network Traffic Analysis
Network traffic analysis helps assess bandwidth usage, detect anomalies, and optimize performance. Tools like NetFlow collect detailed traffic data, enabling IT teams to allocate resources efficiently and enhance security.
Key Features to Consider in Network Monitoring Software
With numerous network monitoring tools available, from open-source to enterprise solutions, choosing the right software is key to maintaining long-term stability and performance. The best systems provide clear visibility into network health, enabling quick issue detection and efficient troubleshooting.
When choosing a network monitoring system, consider the following key features:
- Real-time monitoring and alerting — Identifies problems as they arise and delivers fast notifications;
- Comprehensive network mapping — Displays a visual depiction of the whole network, including drill-down options for specific components;
- Efficient polling engine – Monitors network performance without consuming excessive bandwidth;
- Automatic device discovery — Identifies and integrates new network devices seamlessly;
- Cross-platform compatibility –- Supports multiple operating systems and network setups;
- Customizable dashboards — Displays both real-time and historical data with mobile accessibility;
- Quick setup and configuration – Simplifies deployment to minimize downtime.
Top Network Monitoring Solutions
Choosing the best network monitoring tool may be difficult since different solutions provide varied degrees of detail in performance tracking, issue detection, and device management. To assist focus your search, consider the following popular network monitoring systems (NMS):
- ipMonitor;
- Nagios;
- PRTG;
- ManageEngine OpManager;
- NetFlow Traffic Analyzer;
- Network Performance Monitor.
Integrating application performance monitoring alongside network monitoring enhances visibility into system performance, helping to identify bottlenecks, optimize resources, and ensure a seamless user experience.
Choosing the right network monitoring software leads to more visibility, faster issue response, and overall network efficiency.
Challenges of Network Monitoring
Networks are gradually becoming more complicated, making old monitoring approaches ineffective. Previously, IT staff used manual techniques to handle issues, such as SSH access to servers or remote equipment checks. But these approaches lack detailed information about applications and infrastructure, making it difficult to quickly identify root causes. As networks grow, these manual methods become increasingly impractical.
Cloud environments introduce further challenges. The dynamic nature of cloud workloads and infrastructure increases network complexity. Temporary instances are created and removed based on demand, and their IP addresses change dynamically. This makes it difficult to track network connections using IP addresses alone. Many monitoring tools are unable to track connections between services or pods, limiting visibility.
Another concern is that cloud providers manage the underlying network infrastructure, giving enterprises little control over network difficulties. When issues arise, the only alternative may be to relocate workloads to another availability zone or area until the problem is fixed.
Common Use Cases for Network Monitoring
Network monitoring plays a crucial role in various IT setups, ensuring stability, performance, and security. Below are key scenarios where network monitoring proves beneficial:
Data Center Monitoring
Network monitoring helps engineers track real-time data within data centers, enabling quick detection of critical issues such as:
- Device failures;
- Sudden temperature increases;
- Power outages;
- Network congestion or capacity limitations.
Cloud Network Monitoring
Cloud service providers and IT teams use network monitoring tools to oversee cloud infrastructure performance and interdependencies between applications. These tools help:
- Track traffic movement across different cloud regions;
- Analyze network usage costs from various cloud providers;
- Identify connectivity issues affecting cloud-hosted applications.
This visibility is essential for optimizing cloud network performance and cost management.
Containerized Application Monitoring
With the rise of containerized applications, maintaining network integrity across distributed systems is critical. Organizations using platforms like Kubernetes rely on network monitoring to:
- Ensure smooth communication between containers;
- Detect performance issues across cloud and on-premises deployments;
- Monitor connectivity between microservices.
Conclusion
Network monitoring is critical for ensuring network performance, security, and dependability. It aids in problem detection, downtime prevention, security threat identification, and resource optimization. Monitoring also helps with compliance, troubleshooting, and ensuring uniform operations across several IT systems. Choosing the proper monitoring system enables enterprises to handle issues quickly, reduce interruptions, and maintain network stability as technology evolves.
