Have you ever wondered how network security evolved from the good old days of ISA server to the more advanced version, known as Forefront TMG? If so, you’ve come to the right place. In this article, we’re going to take a stroll down memory lane, discuss what features made ISA so great, what new things TMG brought to the table, and where we are with all of it now.
The Times of ISA Server

If we jumped on a timeback machine and traveled back to the 2000s, we would see how popular Microsoft’s ISA server used to be. Thousands of organizations relied on it to protect their networks. It wasn’t just a firewall. The successor to Microsoft’s Proxy Server 2.0, it combined caching, VPN, antivirus, and proxy services, making it an all-in-one solution for network security.
Despite the popularity of the firewall, in 2010, Microsoft announced an upgrade. An all-fav ISA server was now replaced with Forefront Threat Management Gateway (TMG), a more advanced version of ISA that became Microsoft’s answer to the challenges brought up by the increased demands of the digital world.
Now, you might wonder, “Why change something that works?” Well, sometimes even the best tools need an upgrade to keep up with the times. In the case of ISA, that’s exactly what happened. Microsoft knew it was time to shake things up. The plan was to create a better solution by removing ISA’s limitations and adding a few shiny new features along the way.
What Made ISA Server the Talk of the Town?
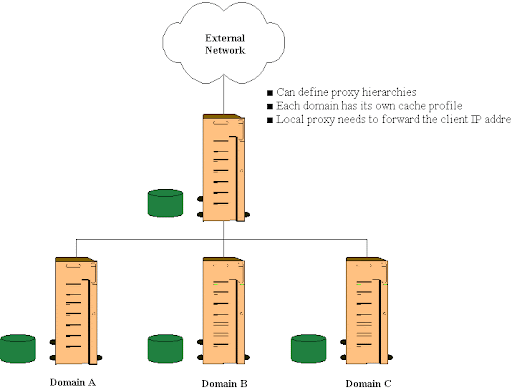
In the early 2000s, ISA Server was a real workhouse. It wasn’t just the features or integration of so many services that made it stand out. It was the fact that it could handle pretty much everything – from caching to VPNs – and also served as a reverse proxy. Organizations could seamlessly integrate it with Microsoft’s environments to create an all-in-one security solution.
However, it wasn’t without its shortcomings. Yes, that’s right, even such great tools like ISA aren’t perfect, though many IT administrators who used it would probably argue with it. The main issue with ISA was that it started hitting its performance limits.
Cyber attacks became more sophisticated and frequent, and ISA, as good as it was, was rather clunky in the face of these threats. That was the time ISA started to show its age. So, even though it had a ton of strengths and so many people loved it – and still do – without a proper tune-up, it wouldn’t be able to cope with today’s highways.
Forefront TMG Stepped Up the Game
As we’ve already mentioned, Microsoft decided to step up the game. They used the strengths of ISA to build a new, refined solution while ironing out its shortcomings. That’s how Forefront TMG was born. A younger sibling of ISA, it had all the tried-and-tested functionalities of ISA but with a host of improvements that made it a real game-changer.
Key Differences and New Features
Those who are familiar with Forefront TMG know that it wasn’t just a facelift – so to speak. The tool came with a whole new set of bells and whistles making it pretty special. Now, on top of the basic functionality, it also offered:
- Enhanced security features;
- Improved caching and logging capabilities;
- Better VPN support;
- Native integration with newer Windows Server versions (like Windows Server 2008 R2).
What’s important is that those upgrades weren’t just minor twists upon an already good product. They were designed to tackle even the most sophisticated cyber threats that were emerging at the time.
Technical Innovations in Forefront TMG
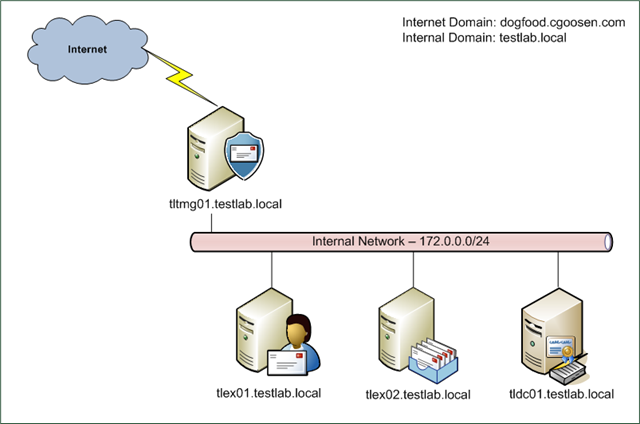
Let’s dig a little deeper and see what exactly Forefront TMG had under the hood. If you’re a techie who loves to geek out over details, here’s the lowdown:
- Advanced Threat Management: TMG came loaded with built-in malware protection and enhanced web filtering features. This add-on made it possible for the server to spot threats long before they could even get a foothold in your network;
- Improved Caching and Logging: With TMG, administrators could better understand network traffic. The logging and reporting features were a far cry from what ISA offered, making it easier to monitor and troubleshoot network activity;
- Enhanced VPN Support: Whether you were connecting from the office or working remotely from any other place in the world, TMG’s upgraded VPN capabilities made it a breeze to set up secure connections;
- Native 64-bit Support and Integration: Built to work seamlessly with Windows Server 2008 and 2008 R2, TMG offered a more modern and scalable platform compared to its predecessor.
Think of it like upgrading your old classic car to a modern electric vehicle. You still have a car to travel where you need to, but unlike the old car, you can do it quicker and more efficiently.
Migration From ISA to Forefront TMG
Switching from ISA to TMG wasn’t as simple as a walk in the park. Before organizations could do it, they had to weigh all the pros and cons, as well as invest time and resources in the process of migration, which came with its own set of headaches as well.
Here are just some of the things that IT teams had to consider:
- Configuration overhaul: Migrating configurations, policies, and rules from ISA to TMG required careful planning. You couldn’t just copy-paste everything over. Migration required a number of tweaks and adjustments that could only be done manually;
- Training and familiarity: IT geeks who were used to ISA had to get up to speed on TMG’s new features and interface, which a) required time; and b) was a pain in the neck considering the high-pressure environments;
- Cost-benefit analysis: While the benefits of TMG seemed rather clear, organizations needed to do their own investigation to understand if the cost of the upgrade would actually be worth it;
- Potential downtime: Last but not least, any migration carries the risk of downtime, which can be a big headache for businesses that rely on network availability.
Despite these challenges, it didn’t take long for a vast majority of companies to switch to TMG. After all, the benefits were far more significant than the risks.
What’s Next After TMG?
The twist in the tale? On April 14th, 2015, Microsoft made an announcement that they decided to call it quits on TMG. The mainstream support ended in 2015, and 5 years later, the extended support wrapped up as well. And while you may feel all bummed out now, know: TMG’s influence is still very much alive.
The legacy of ISA and TMG paved the way for newer security solutions that focus on integrated, multi-layered defenses. Modern alternatives like the Web Application Proxy and Azure Active Directory Application Proxy have become a decent replacement for those looking for a Microsoft-supported solution.
Final Thoughts
So, what’s the takeaway from this evolution journey? Well, this tale is an illustration of how quickly things change in the tech world. Despite how well ISA served us, there came a time when it just couldn’t cope with the threats that were investing in the web. As those threats got thicker, it was clear that something new was needed.
That’s where Forefront TMG stepped in. A polished version of ISA, it became a game-changer in the tech world. Not only did it address the shortcomings of ISA, but it took the game to a whole new level by introducing improved security features and modern integrations.
Here we are, and TMG is just a nostalgic memory, but its influence is still very strong. Many companies still haven’t found a decent alternative that could effectively replace what worked for them for so long.
However, the story of ISA and TMG has taught us an important lesson. You can’t get hold of the old if you want to really get ahead, especially when it comes to your network security. Even if there are a few bumps along the way, embracing the new is essential to stay resilient and competitive.
