Cyber threats are more complex and advanced now, and they happen way more often. So, you need the strongest security measures and best penetration testing tools to protect your business.
These instruments will help you determine vulnerabilities in your network and handle them. We want to tell you more about how they work. So keep reading and find the practical tools you can use.
All about Penetration Testing
Penetration testing is a simulation of a cyberattack. You can do it on a computer system or network to evaluate its safety.
This testing allows you to find weak spots that hackers might use. These instruments also provide recommendations for improving security measures. You can often learn how to work with them in coding bootcamps.
Why this type of testing is so important?
First, it allows you to verify the effectiveness of your security controls, like
- Firewalls;
- Intrusion detection systems;
- Access controls, etc.
These systems may not always function as expected, and pen testing helps validate them in real scenarios.
It also helps you lessen possible financial and reputational damage. A successful breach can result in data theft and loss of customer trust. You can avoid that by recognizing and managing vulnerabilities early.
Regular penetration testing shows stakeholders and customers that you take cybersecurity seriously. This can improve your credibility and trust. Plus, some industries demand it to meet all the compliance norms.
Main Types of Penetration Testing
The purpose of penetration testing tools is pretty straightforward. They help find system weaknesses before hackers do it. You also need to know about its main types, as each of them covers different aspects of security.
Network
This type can evaluate the security of your network infrastructure. You can perform it on internal and external networks to detect vulnerabilities, like
- Weak passwords;
- Misconfigured firewalls;
- Unpatched software.
It helps you prevent unauthorized access and data breaches.
Web Application
Web applications are common targets for cyberattacks. So, this testing focuses on finding security flaws in
- Websites,
- APIs,
- Web services.
Testers usually look for SQL injections, XSS, and insecure authentication mechanisms.
Wireless
Wireless networks might become an entry point for attackers if you don’t protect them properly. So, this kind of pen testing helps you assess the security of Wi-Fi networks and find different risks, including
- Weak encryption;
- Rogue access points;
- Unauthorized devices, etc.
This test helps prevent data interception and unauthorized network access.
Social Engineering
Another huge risk you might face is human error. Social engineering evaluation can help you recognize susceptibility to manipulation tactics, like
- Phishing;
- Impersonation;
- Pretexting.
The goal is to find weaknesses in security awareness and enforce better training programs.
Physical
Physical security is just as important as digital one. This kind of testing lets you examine the main physical defenses, including
- Security guards;
- Access control systems;
- Surveillance.
It helps you find ineffective security measures that might allow others to access sensitive areas.
Cloud
The last type we want to highlight is cloud testing. It helps you assess the safety of cloud-based services and configurations. You can detect misconfigured storage, weak API security, and improper access controls through it.
Top 6 Penetration Testing Tools
Ethical hacking is extremely important for your cybersecurity strategy. You need specialized instruments to make it effective. So, we want to highlight some of the penetration testing tools for you to try out.
Nmap
Nmap is an open-source alternative for penetration testing. It is mostly used for network discovery and security analysis. It can scan both large networks and individual hosts. So, it’s a versatile solution for cybersecurity professionals and system administrators.
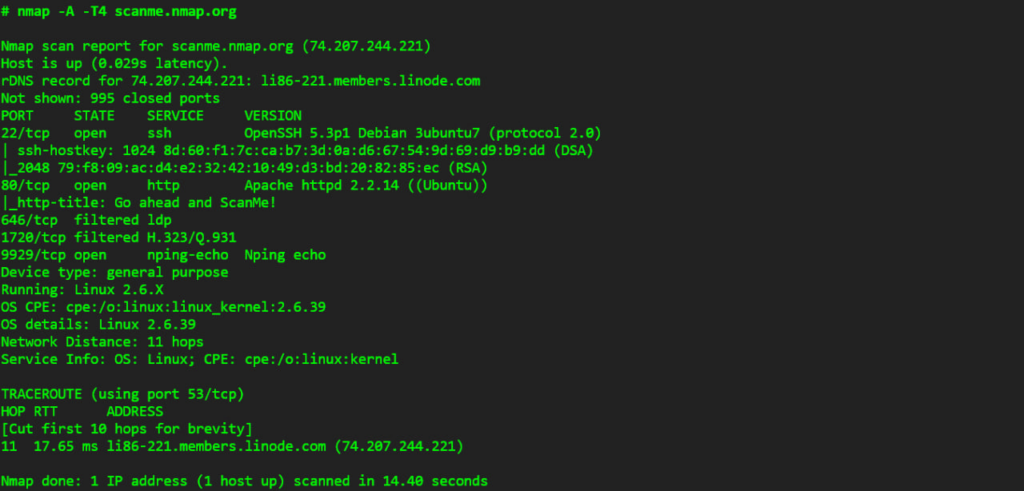
Nmap uses raw IP packets to
- Identify active devices on a network;
- Detect running services;
- Determine operating system details;
- Assess firewall or packet filter configurations.
Its output consists of a detailed report on scanned targets. The main feature here is the “interesting ports table.” This table provides information about each detected port, including its
- Number;
- Protocol;
- Associated service;
- State.
Beyond port scanning, Nmap can offer details on network devices. This makes it a great tool for security assessments and routine network administration.
Metasploit
Metasploit is a popular penetration testing framework. It has a huge library of exploits and payloads. They allow you to simulate real-world cyberattacks.
Some of the features it offers are
- Post-exploitation models;
- Meterpreter shell for deeper penetration;
- Custom payloads option;
- Automated scanning;
- SET integration;
- Cross-platform support.
How does this instrument work?
First, it identifies target systems and collects relevant data. Then it scans and detects security flaws with built-in and third-party tools. Next, it goes through the exploitation and post-exploitation stages. And finally, it generates reports on findings and provides recommendations to lower risks.
Wireshark
The next tool we want to suggest is Wireshark. It’s a network protocol analyzer that you can use for ethical hacking as well.
You can use it to analyze network traffic and identify vulnerable spots. Some of its key functionalities are
- Live packet capture and offline analysis;
- Deep packet inspection;
- Advanced traffic filtering and analysis;
- VoIP analysis;
- Decryption of certain secure protocols, and much more.
Wireshark has a graphical interface with a detailed view of traffic. Plus, it can offer you custom plugins and scripts. They enhance functionality based on specific security needs.
Nikto
Another penetration testing tool you can try is Nikto. It is an open-source web server scanner. You can use it to identify security exposures, outdated software, and misconfigurations in web servers.
Here are the features it can offer you:
- Full-scale scanning;
- SSL support;
- Full HTTP proxy support;
- Different output formats (plain text, SQL, XML, HTML, etc.);
- Anti-IDS invasion technqiues;
- False positive reduction, and more.
Nikto sends HTTP requests to a target web server and analyzes the responses for known vulnerabilities. It compares the responses against its vulnerability database. Then, the tool provides detailed reports for you to take corrective actions.
Burp Suite

The next alternative Burp Suite is a solution for web security testing. Its main tool is Burp Scanner which automates the detection of security flaws.
It uses a sophisticated crawling algorithm that mirrors the approach of a manual tester. This allows it to find hidden vulnerabilities in
- APIs;
- Unstable networks;
- Large applications.
Also, it applies location fingerprinting that reduces redundant traffic and makes scanning faster. You can easily modify it and pick specific vulnerability categories for your requirements.
Plus, Burp Suite can offer you the OAST function. It can detect problems that conventional scanners often miss, like asynchronous SQL injection and blind SSRF. Not to mention its high accuracy with minimal false positives.
Nessus

Another penetration testing tool we want to suggest is Nessus by Tenable. It can offer you diverse scoring systems, including
- CVSS v4;
- EPSS;
- Tenable’s VPR.
This alternative is really user-friendly. It provides detailed tips and next steps through a resource center. So, it’s suitable for security professionals and non-security staff.
Nessus has more than 450 pre-configured templates. So, you can quickly scan for vulnerabilities and gain immediate details on your systems’ security status.
It also allows you to generate custom reports. Plus, this instrument has a unique “Live Results” feature. It automatically conducts offline vulnerability assessments with every plugin update.
How to Find a Suitable Tool?
You already know about the popular penetration tools available. However, you still might have a question – “Which one is the best for me?” So, we gathered a few criteria you should evaluate before choosing.
Type of Testing
Penetration testing can be classified into different types. We described the main ones above. So, you have to find a tool that matches your testing needs. Some instruments deal with specific environments, like cloud infrastructures. Other ones have a more general purpose.
Range of Feature
Next, you have to compare the functionalities of different tools. The main features, you might need are
- Network scanning and mapping;
- Vulnerability scanning;
- Exploitation;
- Detailed and customizable reports.
Ease of Use
The UI of these instruments is another important aspect to weigh. A good tool should be user-friendly and straightforward. It’s especially necessary if you don’t have a deep technical background. Also, make sure it has clear documentation and a strong support community.
Customization
Not all penetration tests are the same. Your choice should be flexible enough to allow customization. You may need the possibility to write your own scripts or modify existing ones. Additionally, check if it integrates with other tools and security systems you have.
Cost
These tools may differ in price a lot. Some of them are free and open-source and some are premium commercial solutions. Evaluate the cost of the tool compared to your budget and the value it will give. Some of the open-source alternatives we highlighted may be better if you have a small team.
Support Resources
Also, make sure that the alternative you pick has strong support resources, like
- Forums;
- Tutorials;
- Shared exploits.
Commercial solutions usually offer a dedicated support team. Open-source ones rely more on community.
Conclusion
Penetration testing is an important component of any cybersecurity startegy. It allows you to find weak areas in your systems before the attackers and fix them.
You can maintain your trustworthy reputation and avoid financial consequences with its help. It’s important to evaluate your needs and resources to find the most suitable penetration tools. There are many free and commercial solutions to pick from.
Hope that our guide was helpful! Try out some of the alternatives we described and maybe you’ll find a fit for your needs.
