Ubiquitous computing is increasingly becoming a key part of modern technology, allowing devices to function intelligently without constant human input. By integrating it into everyday objects, this approach enables automated data collection, communication, and processing across various environments. From smart homes and healthcare systems to logistics and self-driving vehicles, ubiquitous computing enhances efficiency and automation in different industries.
What is Ubiquitous Computing?
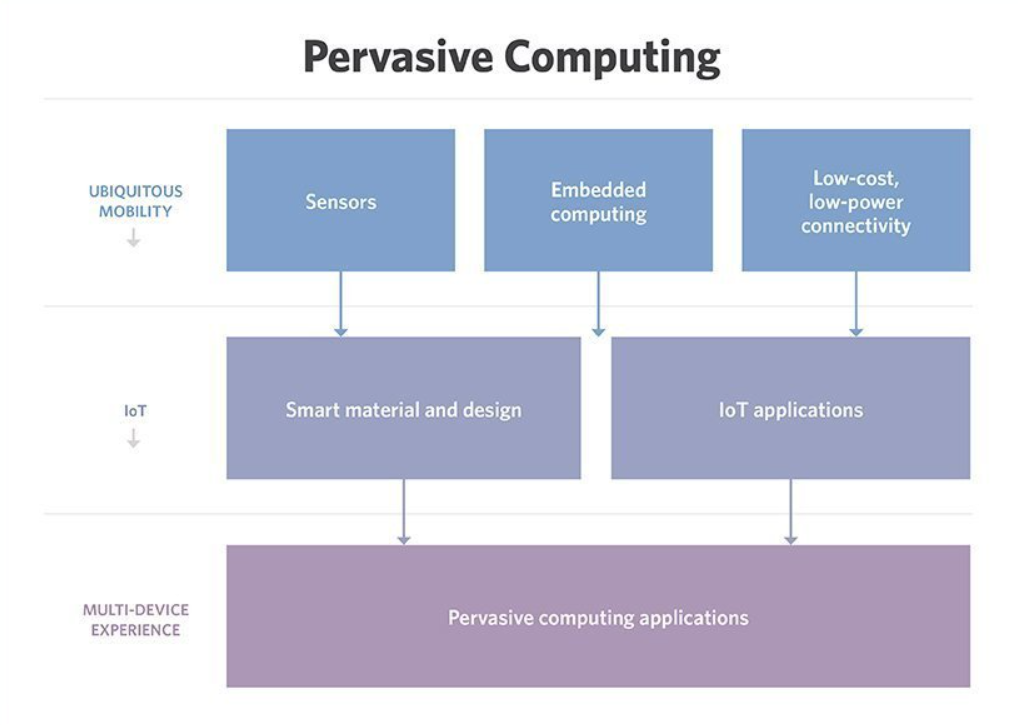
Ubiquitous computing, also known as pervasive computing, is the integration of computer technology into daily products and situations. Unlike conventional computing, which requires direct human contact, ubiquitous computing allows devices to function proactively by anticipating and meeting user demands using AI and machine learning.
Microprocessors are incorporated into everyday objects including lighting, cameras, televisions, wearable technology, voice assistants, and sensors. Across a range of applications, these networked devices improve efficiency through adaptive adaptation and communication. For example, a smart city may enhance urban planning and minimize congestion by combining networked systems like retail establishments, traffic management, and CCTV. Through constant data collection and analysis, ubiquitous computing builds more intelligent, responsive surroundings that improve everyday life.
How Ubiquitous Computing Works
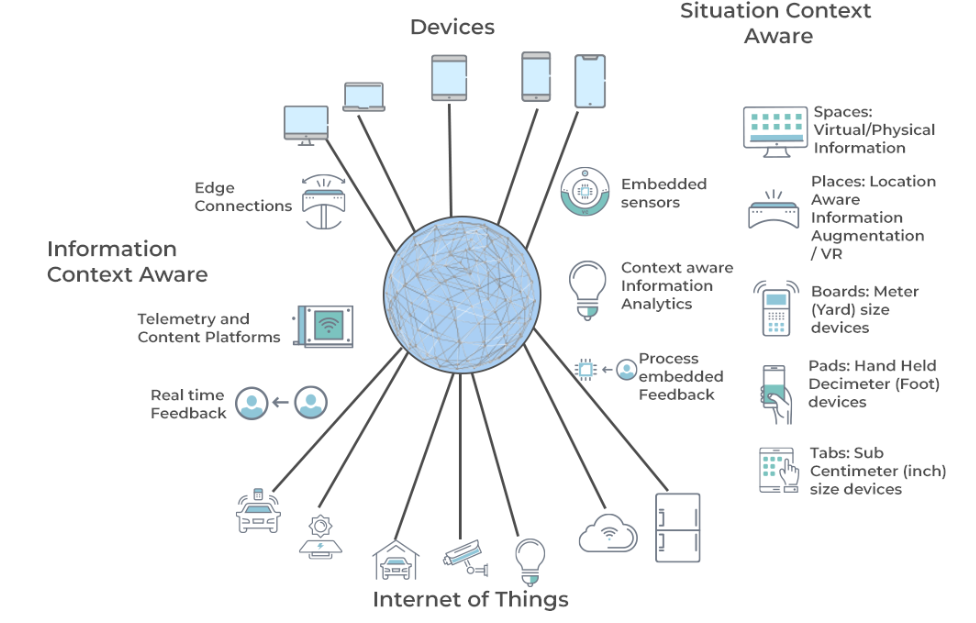
Ubiquitous computing enhances workplaces, homes, and transportation by using real-time data, automation, and digital systems to improve efficiency. It operates in the background, making technology more useful without requiring constant user interaction.
Unlike traditional desktop computing, ubiquitous computing enables devices to function across different locations and networks without direct input. Smartphones, tablets, wearables, and household appliances stay connected, allowing tasks to transfer automatically as users move from one place to another, such as from a car to an office.
A practical example is an autonomous vehicle that detects its passengers using smartphone proximity, charges itself when needed, and processes automatic payments for tolls and parking. Ubiquitous computing guarantees data exchange and real-time communication by integrating microprocessors into gadgets.
The goal of this technology is to simplify how people interact with digital systems by reducing complexity and improving efficiency. As an extension of mobile computing, it connects wireless networks, embedded systems, RFID tags, speech recognition, AI, and automation.
As technology changes, staying informed about advancements is important for businesses and individuals. Understanding how to keep up with technology helps organizations adapt to new developments and use ubiquitous computing effectively.
The concept is also applied in educational settings, where students and teachers use personal, internet-connected devices both at home and in the classroom. As computing hardware continues to shrink in size, its integration into lightweight, portable devices further expands the potential for ubiquitous computing, making digital interactions more intuitive and immersive.
Differences Between Ubiquitous Computing and the Internet of Things
The Internet of Things (IoT) builds on the idea of pervasive computing, but there are key differences. IoT connects everyday objects to the internet, but it still requires users to set up and manage devices. In contrast, Mark Weiser’s vision of ubiquitous computing aimed for fully autonomous systems that function without human input.
Both pervasive computing and IoT allow devices to communicate and provide notifications about their status. IoT aims to integrate computing into common objects, making them connected and interactive. However, IoT systems still need configuration and user input, whereas ubiquitous computing seeks to make technology function in the background without manual intervention.
IoT relies on wireless sensor networks to collect and transmit data. These networks gather information from individual sensors and send it to an IoT server for processing. For example, in infrastructure monitoring, IoT sensors can detect water leaks in pipelines before relaying the data for analysis. In contrast, wearable devices, such as an Apple Watch, send real-time data directly to cloud servers for immediate processing.
Although IoT is moving toward further automation, user management is still necessary. Even if technology is heading toward ubiquitous computing, face-to-face interaction is still necessary.
Benefits of Pervasive Computing
Pervasive computing requires less human interaction compared to ubiquitous computing, where a larger number of connected devices may still depend on manual data extraction and processing.
Since pervasive computing systems collect, process, and communicate data, they can adjust to changing conditions and user activities. This adaptability allows these systems to recognize their environment and improve efficiency, convenience, and overall quality of life.
Essential Elements of Ubiquitous Computing
Understanding the core elements of ubiquitous computing helps explain how these systems work. Each component contributes to making computing more efficient and responsive.
- Sensors and Actuators: Sensors collect data from their surroundings, while actuators use this data to trigger actions. These components enable automation and real-time responses;
- Connectivity: Devices communicate using technologies like Wi-Fi, Bluetooth, and IoT protocols to share and process information;
- Data Processing: Data is analyzed either on the device (edge computing) or through cloud systems, with AI and machine learning improving efficiency in handling large data sets;
- User Interface: Interaction methods go beyond traditional screens and keyboards. Voice commands, gestures, and automated responses allow for hands-free operation;
- Software: Operating systems, applications, and communication protocols coordinate hardware functions and enable devices to work together as a system.
By combining these elements, ubiquitous computing systems adapt to user needs, improving efficiency, convenience, and automation in everyday environments.
Structure of Ubiquitous Computing
Ubiquitous computing is more than just developing new types of computers with enhanced capabilities. It involves creating an interactive system that manages information, communication, and automation in a way that integrates into daily life. This system operates through multiple layers, each handling specific tasks to ensure efficiency and adaptability.
Layer 1: Task Management
This layer analyzes user tasks, context, and dependencies to adjust the environment based on user needs. It determines what configurations are necessary to support specific tasks and reconfigures the system as requirements change.
Task management also monitors user actions and environmental changes, maintaining continuity when tasks are paused and resumed. By collecting and analyzing user task data, this layer helps regulate environmental settings dynamically. For example, if a user moves to a new location, task management ensures that relevant resources and configurations remain accessible.
Layer 2: Environment Management
This layer connects user needs with available resources and system capabilities. It maintains models that translate abstract user demands into concrete system responses.
Environment management helps manage changing conditions by identifying and configuring necessary services, such as voice recognition or automation controls. It continuously updates system configurations based on user preferences and resource availability, ensuring that services remain efficient despite variations in the computing environment.
Layer 3: Environment Control
This layer oversees physical and digital resources, including devices and software applications that assist users in completing tasks. It ensures that available systems function optimally without requiring direct user intervention.
The environment layer translates user needs into specific system actions. It also enables applications to adjust dynamically, responding to changes in workload, resource availability, and user preferences. Ubiquitous computing systems must be adaptable, allowing them to function in varied and unpredictable conditions.
Modern computing environments require systems that adjust to different devices, networks, and user needs. Ubiquitous computing supports diverse applications across workplaces and homes, integrating wireless and wired communication to ensure continuous operation. As resources change, these systems must adapt efficiently, maintaining reliability across different locations and computing conditions.
Uses of Ubiquitous Computing
Ubiquitous computing is integrated into various industries, enhancing automation, efficiency, and decision-making. It connects devices, sensors, and systems to improve logistics, security, healthcare, and more. Below are key applications of ubiquitous computing.
Logistics
Ubiquitous computing connects physical transportation with digital tracking, allowing businesses to monitor goods in real time throughout the supply chain. Sensors collect and analyze data on raw materials, partially finished products, and final goods.
Advanced data processing techniques, including logic programming and machine learning, help improve logistics by predicting and responding to changes. In manufacturing, these sensors also help maintain efficiency and product quality by detecting environmental factors that could impact items during transit.
Self-Driving Vehicles
Autonomous vehicles rely on ubiquitous computing to analyze and respond to real-time data. These systems assist with navigation, driving decisions, and safety monitoring. Inside the car, technology adapts to driver preferences, manages mobile device interactions, and ensures a comfortable ride.
Home Automation
Smart home devices, such as intelligent lighting, locks, and thermostats, use ubiquitous computing to automate daily tasks. These systems adjust settings based on user behavior, improving energy efficiency and convenience. Home automation reduces the need for manual control over heating, ventilation, and security, making living spaces more adaptive and efficient.
E-Commerce
Smart systems in e-commerce use location-based services, automated transactions, and AI-driven recommendations to improve customer experiences. Businesses use smart technology to transition from product ownership to rental models and enable autonomous service management through pervasive computing. This adaptability ensures businesses can respond to changing market demands.
However, despite the advantages of smart technology, many companies struggle to sustain growth due to strategic missteps. Understanding the top reasons businesses fail can help organizations use ubiquitous computing effectively and avoid common pitfalls.
National Security
Ubiquitous computing is used in identity verification systems such as electronic passports and smart cards. It also plays a role in security surveillance, monitoring critical infrastructure like airports and power grids. Advanced tracking and recognition technologies improve threat detection and response capabilities.
Medical Technology
Wearable health devices and smart implants monitor patient conditions in real time, allowing for early detection of health issues. Ubiquitous computing helps in disease monitoring, behavior tracking, and remote patient care. These systems improve healthcare accessibility and enable personalized treatment plans.
Military Applications
The military uses ubiquitous computing for real-time intelligence gathering, threat detection, and strategic planning. Networked defense systems rely on data-driven decision-making to enhance battlefield awareness. These technologies improve situational analysis, secure communication, and automated surveillance in modern warfare.
Ubiquitous computing continues to evolve, providing smarter, data-driven solutions across industries. It enhances automation, security, and efficiency by integrating computing power into everyday systems.
Impact Across Industries
Ubiquitous computing improves efficiency, automation, and decision-making in a variety of businesses. It improves operations, security, and consumer experiences across several sectors.
- Manufacturing: Smart factories use connected machines to automate production, monitor systems in real time, and reduce downtime with predictive maintenance;
- Retail: Retailers manage inventory more efficiently, personalize shopping experiences, and improve supply chain operations to enhance customer service;
- Agriculture: Sensors monitor soil conditions and crop health, allowing for precise irrigation, fertilization, and pest control to increase yield;
- Education: Smart classrooms and adaptive learning platforms provide interactive and personalized learning experiences for students;
- Financial Services: Banks analyze real-time data for fraud detection, security, and personalized banking services, improving mobile banking experiences;
- Transportation & Logistics: Smart traffic systems and real-time tracking enhance road safety and make supply chain management more efficient;
- Healthcare: AI-powered diagnostics, remote patient monitoring, and data analysis improve medical research and personalized treatment plans;
- Environmental Monitoring: Sensors track pollution levels, wildlife activity, and ecosystem changes, supporting conservation efforts and policy decisions.
Conclusion
Ubiquitous computing is becoming more common across industries, enabling devices to function with minimal user input. By embedding technology into everyday objects, it improves automation, efficiency, and data processing in areas like healthcare, logistics, and security. As its use expands, businesses, governments, and individuals are adopting interconnected systems to improve operations and daily tasks. However, security and system compatibility remain challenges as these technologies continue to grow.
